Cyber Unity Learning
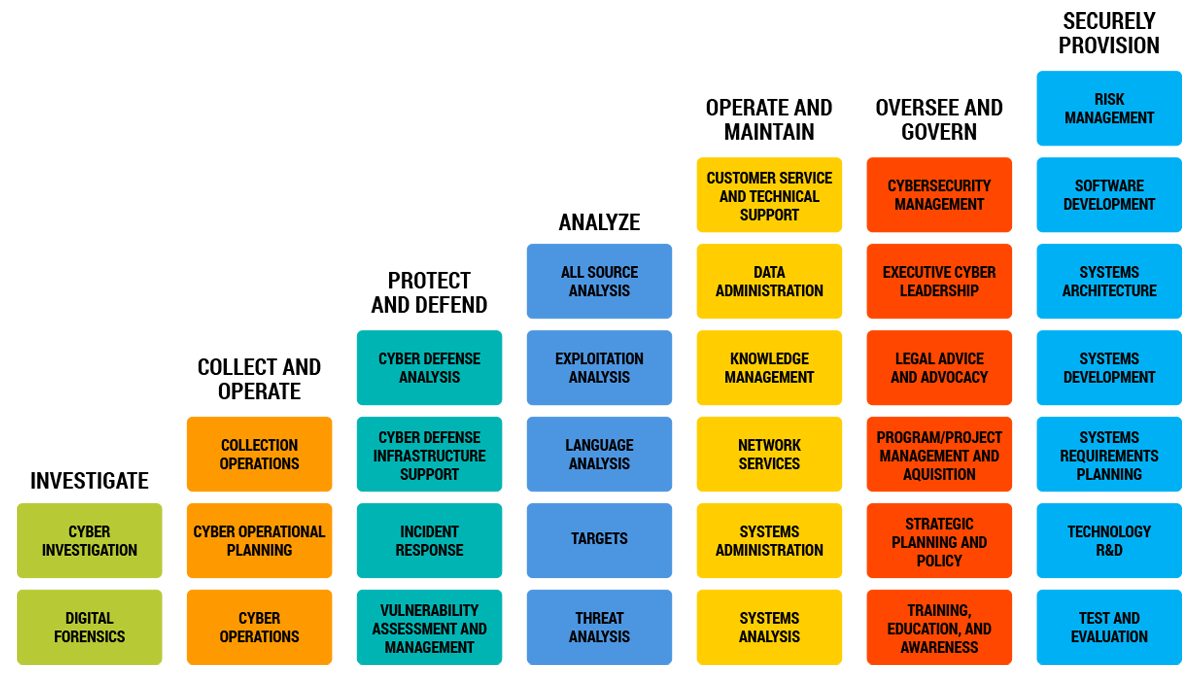
National Initiative for Cybersecurity Education (NICE)
We plan to establish an online community using cloud services such as Microsoft 365, Amazon Web Services where we can share and plan to release training curriculum that teaches candidates how to conduct cybersecurity jobs with specific focus on defensive cyber space operations. We are currently evaluating the best platform to use for this concept that minimizes development time while ensuring that progress across discrete subject areas can be measured, tracked, and reported.
We then plan to use live events to allow candidates to unify and participate in the defense or attack of test infrastructure we will build. All of this leads to a measured test (based on age and skill level) against the NICE Framework for a certification in a skill area or work role of their choice resulting in an actual certification showing they successfully can perform their job role(s) leading to expedited hiring for a cybersecurity job function at a partner organization who believes in our approach. We believe this will require either a twelve (12) or twenty-four (24) month commitment from the individual to complete the process as we describe in the next section. While our initial interest targets individuals and young adults in high school or college (ages 14 – 20), ultimately, we are interested in bringing opportunities to under privileged individuals in low-income areas especially those who do not have daily access to technology at home or at school.
Get Started
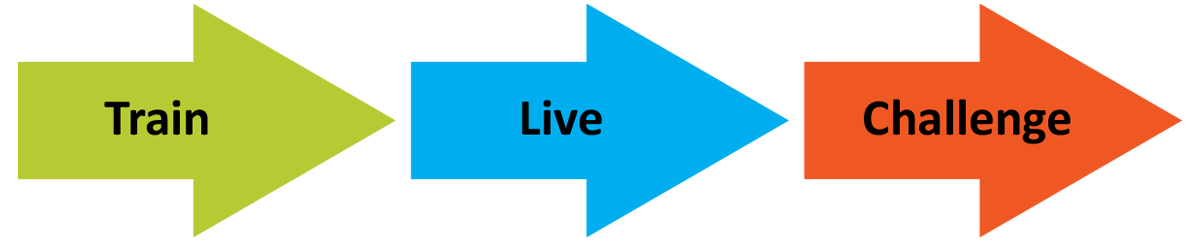
Interested? Get involved in Cyber Unity. Start by signing up here. Our process is simple: Train | Live | Challenge. You can start by taking and reviewing some training material. Next, you then participate in an in-person challenge with a live kit. And finally, you end this part of your cybersecurity learning journey with a grand challenge where multiple groups compete against each other.

Get started, get involved and sign up!
Sign up to get started, get involved and to learn more about how you can be a part of Cyber Unity!
Cyber Unity is a process, a place, and a future certification where an interested individual can unite with others and get access to the skills, training, practice, and certification they need to begin a career in cybersecurity and defensive cyberspace operations.
Quick Links
Contact Us
RX5 Cyber EnVision Cyber Unity Center
3317 Atlantic Avenue
Atlantic City, New Jersey 08401
United States CyberPoint Cyber Unity Center
7142 Columbia Gateway Drive, Suite 100
Columbia, Maryland 21046
United States Phone: + 1 609.233.7942
Email: contactus@cyberunity.tech